Frequently Asked Questions
Here you will find helpful information, please do ask Graham or Max if you'd like to have other specific help added.
It doesn’t matter. You just need to follow the link provided by the teacher and it will work in the browser. It works best in Google Chrome.
Yes we do, but we recommend using Google Meet.
You have a couple of options, you can upload them into Google Drive, Katie has created a simple guide for this or you can use the Sophos VPN, see FAQ below.
This is most likely caused by your browser's popup blocker settings. See below for some helpful information.
If Staff or Students have forgotten a password then Staff should firstly check the Central Register for students, and for staff forgotten passwords, please email Max or Graham.
The security of school data is paramount. See below for information to help you stay safe and secure on-line.
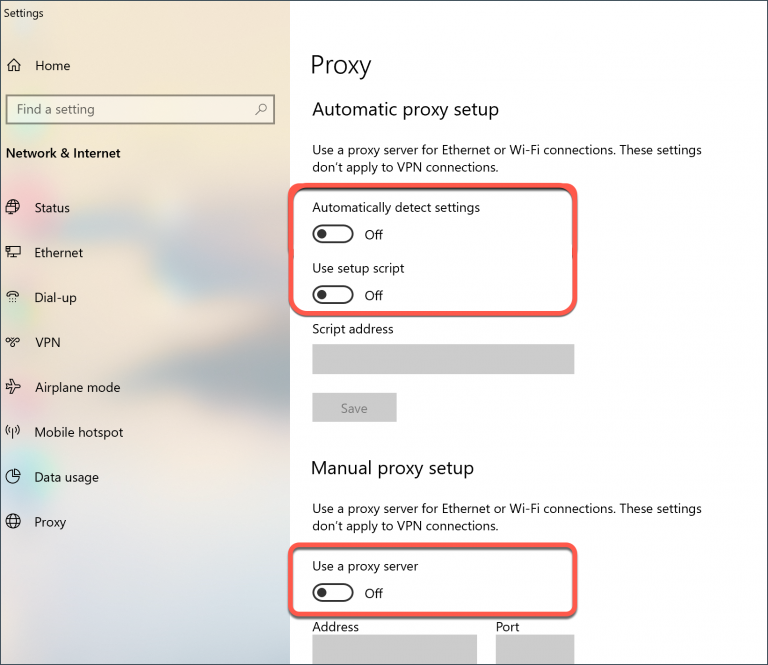
You must turn off the "Use a proxy server" setting on the computer.
• Set the switch under Use a proxy server to off, then click on Save.
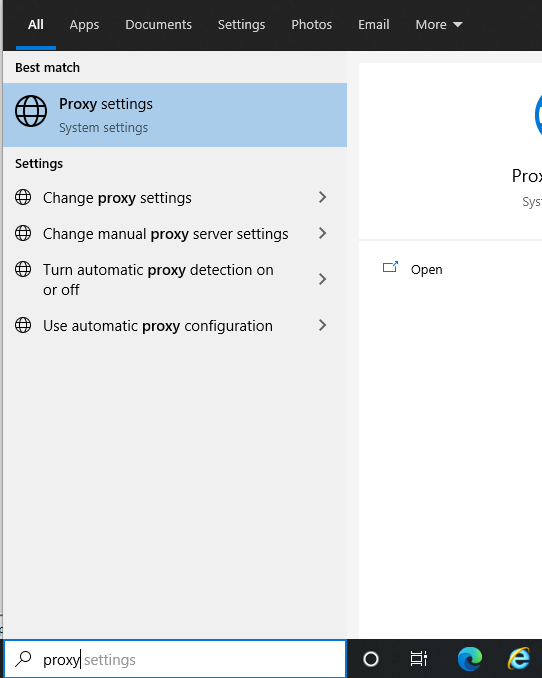
To access the Proxy Settings, just type proxy in the search box and then select "Proxy settings".
• Set the switch under Use a proxy server to off, then click on Save.

The school uses a Sophos VPN (Virtual Private Network) which allows you to securely connect to the school network allowing access to file shares etc.
Note: The SSL VPN requires MFA (Multi-Factor Authentication), often know as 2FA (Two Factor Authentication). Most mobile devices have Authentication Apps available for this.
Here are some recommendations:
Android Free OTP - GET IT HERE
Apple Free OTP - GET IT HERE
Android Google Authenticator - GET IT HERE
Apple Google Authenticator - GET IT HERE
So, what is 2FA / MFA?.
Let's first answer; what is two-factor authentication (2FA)? When users request access to applications and services, 2FA acts as an extra layer of security for ensuring that they are who they say they are. The concept of two-factor authentication isn’t new. It’s been used for years in many areas. In fact, most of us use it all the time when we use an ATM or debit card. The card is "something we have" and the PIN is "something we know" and the two work together to authenticate the user more securely than the card alone.
Traditionally, 2FA is associated with a broader concept of multi-factor authentication (MFA) where authentication requires more than one factor. Factors are usually categorised as:
MPS VPN Setup Instructions for Windows & Mac OS
Here are some recommendations:
Android Free OTP - GET IT HERE
Apple Free OTP - GET IT HERE
Android Google Authenticator - GET IT HERE
Apple Google Authenticator - GET IT HERE
So, what is 2FA / MFA?.
Let's first answer; what is two-factor authentication (2FA)? When users request access to applications and services, 2FA acts as an extra layer of security for ensuring that they are who they say they are. The concept of two-factor authentication isn’t new. It’s been used for years in many areas. In fact, most of us use it all the time when we use an ATM or debit card. The card is "something we have" and the PIN is "something we know" and the two work together to authenticate the user more securely than the card alone.
Traditionally, 2FA is associated with a broader concept of multi-factor authentication (MFA) where authentication requires more than one factor. Factors are usually categorised as:
- Something you have - a credit card, mobile phone or hard token
- Something you know - most typically a password or PIN
- Something you are - biometrics like a fingerprint, retina, or facial pattern
MPS VPN Setup Instructions for Windows & Mac OS
In a strong password, length is the key element that really makes a diffrence.
... Each character you add to your password length, the harder it is to guess or crack ...
... Each character you add to your password length, the harder it is to guess or crack ...
How long does it take to crack a password?
The time it takes to crack a password depends on a lot of factors, such as computer speed, but as a guide:| Password length | Approximate time to crack |
|---|---|
|
7 characters |
< 1 Second |
|
8 characters |
~ 5 Hours |
|
9 characters |
~ 5 Days |
|
10 characters |
~ 4 Months |
|
13 characters |
~ 10 Years |
|
16 characters |
~ 200 Years |
Common ways that passwords are stolen!
A range of methods to attempt to steal passwords, can include:- Shoulder-surfing: someone watching you closely as you log in and attempting to remember the keys you used.
- Key-logging: a device (or piece of software) installed by an attacker to intercept the passwords you type in.
- Social engineering: an attacker trying to convince you to reveal your password to them.
- Guessing: an attacker simply using information they know about you to guess your password.
- Physical searching: an attacker searching the area around your device for insecurely stored passwords (e.g. written down).
- Network searching: an attacker scanning the ICT systems for insecurely stored password information.
- Intercepting: an attacker ‘breaking in’ to information transmitted over a network (including the internet) and looking for password details.
- Brute force: an attacker using a system to try millions of different passwords automatically to attempt to find the correct one.